In today’s rapidly evolving professional landscape, the demand for targeted skills and efficient learning pathways has never been greater. Enter bootcamps—a dynamic approach to education that’s redefining how individuals acquire in-demand skills for a successful career. With an emphasis on intensive learning, career-focused education, and fast-tracking skills, bootcamps are emerging as a powerful means of rapid skill acquisition in a variety of fields.
Gone are the days when a traditional four-year degree was the only path to professional success. In this era of innovation, where industries could transform in the blink of an eye, bootcamps have emerged as a compelling alternative. These programs typically offer an accelerated journey to proficiency, enabling learners to quickly gain skills and knowledge and enter the workforce with a competitive edge.
In this article, we’ll delve into the world of bootcamps, exploring their essence of intensive learning and their laser-focused approach to career-oriented education. Whether you’re a recent high school graduate, a career changer, or someone looking to stay ahead of the curve, join us on a journey to uncover the potential of bootcamp courses.
What Are Bootcamps?
Bootcamps are intensive, short-term education programs that focus on teaching specific skills or subjects within a condensed timeframe. These programs are designed to provide practical, hands-on learning experiences and job-ready training geared to equip individuals with the skills needed for a particular job or career path. Bootcamps typically prioritize real-world application, experiential learning, and industry relevance.
Bootcamps typically cover a wide range of subjects, including coding, data science, digital marketing, cybersecurity, design, healthcare, and more. They aim to bridge the gap between traditional education and the rapidly changing needs of the job market. Bootcamps often emphasize project-based learning, collaboration, and building a portfolio of work to showcase to potential employers.
Key Characteristics
Key characteristics of bootcamps include:
- Short duration: Bootcamps are typically shorter than traditional degree programs, lasting anywhere from a few weeks to a few months. This condensed timeframe could allow participants to quickly acquire skills and enter the workforce.
- Intensive learning: Bootcamps provide an intensive and immersive education, focusing on hands-on experiences and practical training. Participants often spend a significant portion of their time working on real-world projects.
- Focused curriculum: Bootcamps have a specific and focused curriculum—bootcamp courses are tailored to the skills required for a particular job or industry. They cut out general education courses and dive directly into the relevant content.
- Industry alignment: Bootcamps are often developed in collaboration with industry experts and employers. This could help ensure that the bootcamp courses are up-to-date and aligned with current industry trends and demands.
- Flexible learning options: Bootcamps may be offered in various formats: there are in-person bootcamps and online bootcamps, as well as bootcamps that are full-time, part-time , and self-paced. This flexibility caters to a diverse range of learners and schedules.
- Job placement support: Many bootcamps offer job placement assistance, resume building, interview coaching, and networking opportunities to help participants with career transition after completing the program.
It’s important to research and choose reputable bootcamp providers to ensure that the program’s quality, content, and learning outcomes align with your career goals and expectations.
Diverse Bootcamp Domains
The world of bootcamp education is expansive, catering to a multitude of career paths. Aspiring coders could immerse themselves in coding bootcamps, gaining proficiency in programming languages like Python, JavaScript, and Ruby. Meanwhile, web development bootcamps delve into the art of crafting interactive and visually appealing websites, encompassing frontend and backend technologies.
Venturing into the realm of data science, bootcamps equip learners with the analytical skills required to mine insights from complex datasets. Design bootcamps nurture creative talents, teaching the principles of user experience (UX) and user interface (UI) design. Digital marketing bootcamps, on the other hand, guide participants through the intricacies of online advertising, social media strategies, and SEO techniques.
Advantages of Bootcamps
Bootcamps, whether they’re focused on coding, data science, digital marketing, or other fields, offer several advantages that make them an appealing option for individuals seeking to quickly gain practical skills and enter the workforce. Here are some of the key advantages of bootcamps.
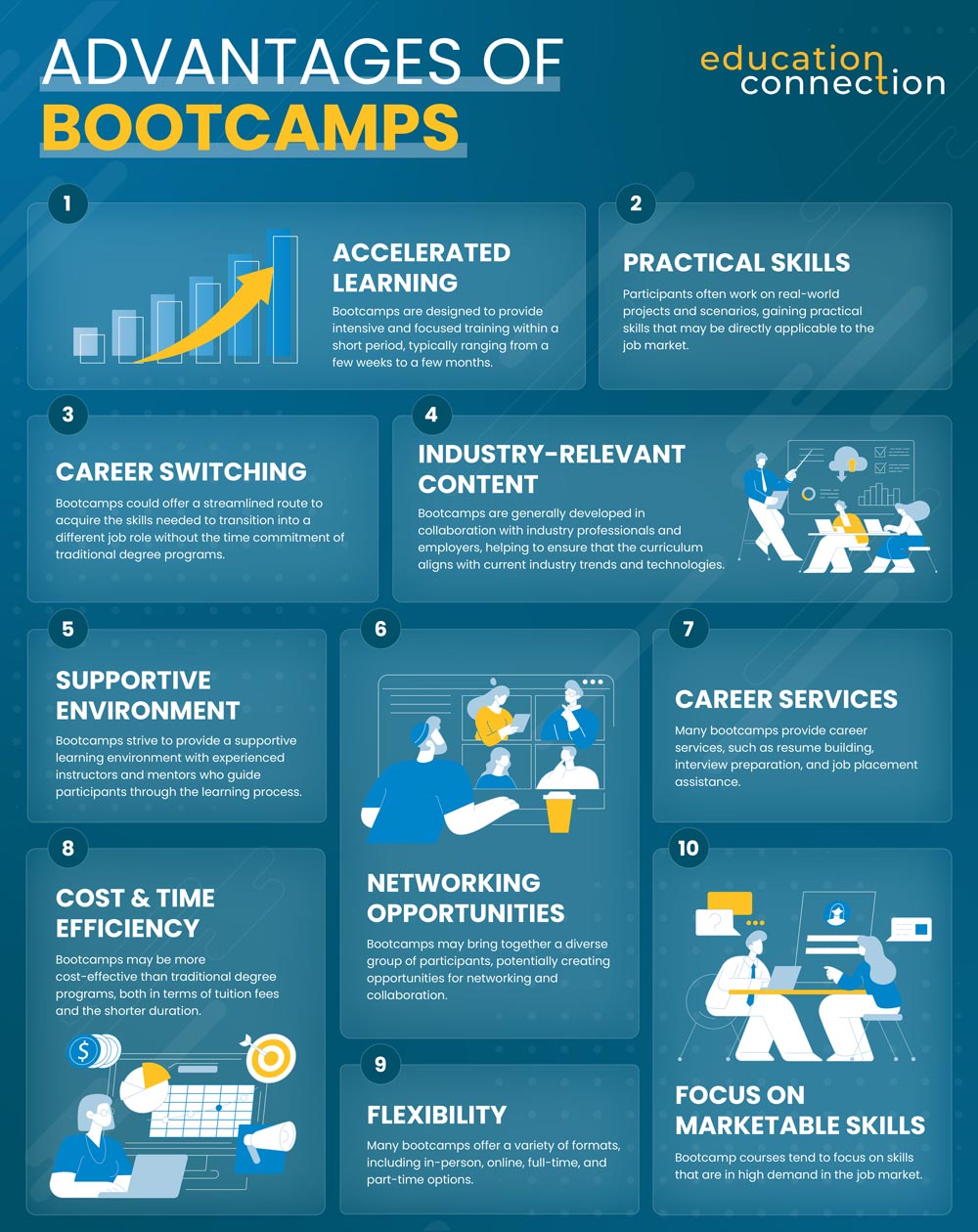
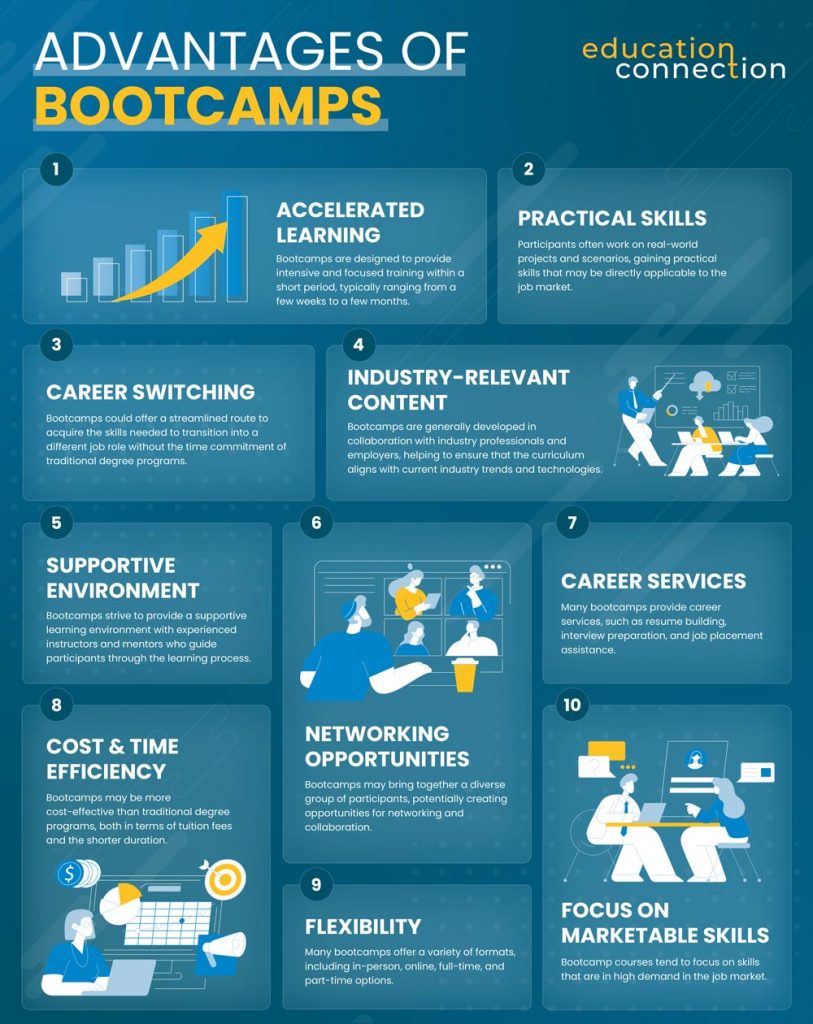
- Accelerated learning: Bootcamps are designed to provide intensive and focused training within a short period, typically ranging from a few weeks to a few months. This accelerated learning format allows participants to acquire necessary skills in a condensed timeframe.
- Practical skills: Bootcamps are known for their hands-on, project-based approach. Participants typically work on real-world projects and scenarios, gaining practical skills that may be directly applicable to the job market.
- Industry-relevant content: Bootcamps are often developed in collaboration with industry professionals and employers. This helps to ensure that the curriculum aligns with current industry trends, tools, and technologies, making graduates more marketable to potential employers.
- Career switching: Bootcamps could provide a pathway for individuals to switch careers or enter a new field. They offer a streamlined route to acquire the skills needed to transition into a different job role without the time commitment of traditional degree programs.
- Networking opportunities: Bootcamps may bring together a diverse group of participants, potentially creating opportunities for networking and collaboration. Connecting with classmates, instructors, and industry professionals could lead to helpful contacts and potential job opportunities.
- Supportive environment: Bootcamps strive to provide a supportive learning environment with experienced instructors and mentors who guide participants through the learning process. This support helps participants overcome challenges and stay motivated.
- Career services: Many bootcamps provide career services, such as resume building, interview preparation, and job placement assistance. This might be particularly beneficial for those looking to secure employment quickly after completing the program.
- Cost and time efficiency: Bootcamps may be more cost effective than traditional degree programs, both in terms of tuition fees and the shorter duration. This could make them an attractive option for individuals looking for a faster return on investment.
- Flexibility: Many bootcamps offer a variety of formats, including in-person, online, full-time, and part-time options. This flexibility allows participants to choose a program that could fit their schedule and learning preferences.
- Focus on marketable skills: Bootcamp courses tend to focus on skills that are in high demand in the job market. This focus on specific, job-relevant skills could increase graduates’ chances of securing employment in their chosen field.
Who Should Consider Bootcamps
Bootcamps have gained prominence as a dynamic solution for individuals seeking to acquire specific skills, change careers, or stay current in an ever-changing professional landscape.
Bootcamps are not limited to a single demographic; they cater to a broad spectrum of individuals with varying aspirations and goals. Recent graduates find value in bootcamps as a means to bridge the gap between their academic qualifications and the practical skills required by employers. These immersive programs empower them to enter the workforce with a competitive edge, ensuring a smoother transition from academia to industry.
For career switchers, bootcamps provide a streamlined route to enter a new field without committing to a full-fledged degree program. Professionals seeking career enhancement and career growth within their current roles could leverage bootcamps to acquire focused skills that enhance their contributions and open doors to new opportunities. Additionally, lifelong learners and enthusiasts looking to explore new interests find bootcamps to be an accessible and engaging way to gain hands-on experience.
Because one of the standout features of many bootcamps is their flexibility, they may be an attractive option for individuals with busy schedules. Many bootcamps offer part-time, online, and self-paced formats, allowing learners to balance their education with existing commitments. This accessibility democratizes learning, enabling individuals from various walks of life to engage with educational opportunities that might have been otherwise unattainable.
Furthermore, the fast-paced nature of bootcamps is particularly suited for those looking to adapt swiftly to industry changes. With their focused curriculum and practical approach, bootcamps compress the learning curve, equipping participants with relevant skills in a short span.
Want to use this Bootcamp infographic on your site? Just use the code below!
Choosing the Perfect Bootcamp
With the vast array of bootcamps, finding one that aligns with your goals could be a pivotal step in your educational journey. As you embark on this path, here are some tips that could guide you in making an informed choice to help maximize your learning experience.
Researching Course Content and Curriculum
The heart of any bootcamp lies in its curriculum. Before enrolling, dive deep into the content of bootcamp courses it resonates with your learning objectives. Scrutinize the topics covered, the depth of material, and the relevance to your desired field. A curriculum should encompass both foundational concepts and advanced techniques, preparing you to tackle real-world challenges.
Evaluating Instructor Qualifications
The quality of instruction could directly impact your learning outcomes. Investigate the qualifications and expertise of the instructors who will guide you through the program. Instructors with practical industry experience and a deep understanding of the subject matter could enhance the value of the bootcamp, offering industry insights that textbooks alone might not provide.
Considering Student Reviews and Testimonials
Peer feedback could offer insights into the effectiveness of a bootcamp. Delve into student reviews and testimonials to gauge the overall satisfaction level and experiences of past participants. Candid insights from those who have walked the same path could provide a realistic view of the bootcamp’s strengths, weaknesses, and the kind of support you could expect.
Analyzing Job Placement Rates and Alumni Success
A significant measure of a bootcamp’s success lies in the employability of its graduates. Investigate the bootcamp’s job placement rates and alumni success stories. High job placement rates might indicate that the bootcamp equips students with the skills needed to secure meaningful employment in their chosen fields. Alumni success stories could showcase how the bootcamp’s training translates into real-world achievements.
Aligning with Personal Learning Goals
Each learner’s journey is unique, driven by personal aspirations and goals. Ensure that the bootcamp you choose aligns with your specific career objectives. Whether you’re seeking to switch careers, upskill within your current role, or explore a new field, the bootcamp should offer a curriculum that caters to your needs.
The format of the bootcamp is another critical factor to consider. Evaluate whether the bootcamp offers in-person, online, part-time, or full-time options that accommodate your schedule and learning preferences. Flexibility in learning format could ensure that you are able to seamlessly integrate education into your life.
Navigating the Bootcamp Journey: Challenges and Considerations
While there are many benefits to bootcamps, it’s important for aspiring bootcamp participants to be aware of the challenges that come along with this fast-paced learning experience.
The Intensity of the Curriculum
One of the defining characteristics of bootcamps is their fast-paced curriculum. The condensed nature of these programs means that you’ll typically be exposed to a significant amount of information in a short span of time. This could be both exciting and overwhelming. To tackle this challenge:
- Stay organized: Keep track of your learning materials, assignments, and progress. Create a study schedule that breaks down each topic into manageable portions.
- Prioritize learning: Understand that not every concept could be mastered instantly. Focus on grasping the core concepts before moving on to more advanced topics.
- Practice regularly: Consistent practice may be key to retaining knowledge. Set aside time each day for coding exercises and projects.
Time Commitments
Bootcamps often demand a substantial time commitment. Balancing the demands of the bootcamp with your personal and professional responsibilities might be a real challenge. Here’s how to manage your time effectively:
- Set realistic expectations: Acknowledge that the bootcamp could require a significant time investment. Communicate your commitment to friends and family so they understand your schedule.
- Time management: Plan your days carefully. Allocate specific blocks of time for learning, practice, breaks, and other commitments.
- Avoid burnout: Remember that quality is usually more important than quantity. Overloading yourself might lead to burnout. Take breaks and engage in activities that help you recharge.
Financial Investment
While bootcamps offer an expedited path into the tech industry, they might come with a hefty price tag. Managing the financial aspect could be challenging, but there are ways to ease the burden:
- Research payment options: Many bootcamps offer flexible payment plans, scholarships, or income-sharing agreements. Explore these options to determine what works for your financial situation.
- Budget wisely: Plan your expenses throughout the bootcamp duration. Cut down on unnecessary costs and prioritize expenditures.
- Consider the ROI: Think of the bootcamp as an investment in your future. Research the average salaries for bootcamp graduates in your desired field to assess the potential return on your investment.
Managing Expectations
It’s easy to approach a bootcamp with sky-high expectations. While these programs may be transformative, it’s important to manage your expectations realistically:
- Embrace the learning curve: Understand that you’re embarking on a journey of growth. Mistakes and challenges are part of the learning process.
- Celebrate small wins: Acknowledge your progress, no matter how incremental it might seem. Each small achievement brings you closer to your goals.
- Be patient: Mastery takes time. Don’t expect to be an “expert” by the end of the bootcamp. Instead, focus on building a strong foundation that you could continue to build upon.
Staying Motivated
Bootcamps may require sustained motivation to overcome the hurdles and complete the program successfully. Here’s how to keep your motivation levels up:
- Set clear goals: Define your short-term and long-term goals. Having a clear vision of what you’re working toward could keep you motivated during challenging times.
- Find a support system: Connect with fellow bootcamp participants, mentors, or online communities. Sharing your experiences and challenges with others may provide emotional support.
- Celebrate progress: Regularly reflect on how far you’ve come since the start of the bootcamp. Recognizing your growth could reignite your motivation.
Maintaining Work-Life Balance
The intensive nature of coding bootcamps might blur the lines between work and personal life. Striking a balance may be crucial for your overall well-being:
- Set boundaries: Define clear boundaries between your bootcamp commitments and personal time. Avoid the temptation to work around the clock.
- Prioritize self-care: Allocate time for activities you enjoy outside of coding. Engage in exercise, hobbies, and spending quality time with loved ones.
- Practice mindfulness: Incorporate mindfulness techniques into your routine to stay grounded and reduce stress.
Beyond the Bootcamp: Navigating the Path of Continuous Learning and Growth
Completing a coding bootcamp is a significant accomplishment that could equip you with the skills and knowledge needed to embark on a career in the dynamic world of software development. However, the journey generally doesn’t end there. In fact, it could be just the beginning of a lifelong commitment to continuous learning, growth, and professional development.
Embracing Continuous Learning
The tech industry is constantly evolving, with new programming languages, frameworks, and tools emerging regularly. As a graduate of a coding bootcamp, staying up-to-date with these industry trends may be critical for remaining competitive in the job market. Here’s how you could make continuous learning a cornerstone of your post-bootcamp journey:
- Read and research: Regularly read blogs, articles, and online resources to stay informed about the latest developments in technology. Follow thought leaders and industry experts to gain insights into emerging trends.
- Online courses: Enroll in online courses, tutorials, and workshops to expand your skill set. There are a plethora of options.
- Personal projects: Undertake personal projects that align with your interests. This not only solidifies your learning but also showcases your skills to potential employers.
Networking within the Field
Building connections with professionals in your field could open doors to job opportunities, collaborations, and mentorship. Here’s how you might effectively network after completing your bootcamp:
- Attend tech meetups and conferences: Participate in local meetups and conferences related to coding, development, and technology. These events could provide excellent networking opportunities and a chance to learn from industry leaders.
- Use online platforms: Join online communities, forums, and social media groups related to your areas of interest. Engage in discussions, ask questions, and share your insights.
- Connect with alumni: Reach out to fellow bootcamp graduates. They could provide insights, advice, and potential connections in the industry.
Pursuing Further Education
While a coding bootcamp is designed to provide a solid foundation, some individuals might feel the need to deepen their knowledge further. Advanced bootcamp programs and further education options could help you stand out in a specific area or gain a deeper understanding of complex concepts:
- Advanced bootcamps: Many bootcamp providers offer advanced programs that focus on targeted skills or advanced topics. These programs could help you further refine your skills and knowledge.
- Formal education: Consider pursuing a formal degree in computer science or a related field if you’re looking to build a strong academic foundation. This option might be particularly appealing if you’re aiming for more research-oriented roles.
Building a Portfolio
As you continue your journey in the tech industry, a well-constructed portfolio could become an important asset. A portfolio is meant to showcase your skills, projects, and accomplishments, providing potential employers with tangible evidence of your capabilities.
Conclusion
Whether you’re a recent graduate, a career switcher, a professional seeking career growth, or simply someone with an insatiable curiosity, bootcamps could offer an impactful educational journey as well as taking a graduate degree programs. With their flexible learning options and industry-relevant curricula, bootcamps stand as a testament to the power of accessible, adaptable, and targeted education in the modern world.